On my Resume page, you’ll find only an image as the page content. But the resume is there–this is actually a resume CTF game!
🏁🚩 Flag Notes
There are two flags in this CTF! One is easier to find than the other, but it’s also not a text resume.
🧱 Walkthrough Structure
Throughout this walkthrough, I’m interspersing information about CTF history and how the web works, but I’m also trying to keep that content visually separate from the step-by-step how-to. You can jump right into the Let’s Play part and skip all the introductory information.
If you have recommendations, I would love feedback on the walkthrough for better readability! Let’s jump into it!
What’s a CTF?
A CTF, or capture the flag, is a cybersecurity exercise (or game) in which “flags” are secretly hidden in insecure applications, websites, or even other hardware and devices like cars in DEFCON’s Car Hacking Village CTF. Competitors steal flags either from other competitors or from the CTF creators. There are other kinds of CTFs these days, though!

The first known instance of this kind of CTF was at DEF CON 4 in 1996, although it seems likely they occurred earlier without the judging and labels. You can even watch recordings of the CTFs the DEFCONConference YouTube Channel.
How to CTF
Know Your Target & Its Tech
In security, you often take the role of the Investigator. 🔍 Investigators don’t have all the answers when they start an investigation. They need to piece together all the data they do have.
When you start out, you have to truly investigate, test things, poke and prod at things to gain clues. CTFs encourage step-by-step methodologies because there is truly no other way to move forward or pivot to other avenues of investigation if you don’t start with the basics. This is also why hackers lover to recommend reading Sherlock Holmes. It’s all about your investigative mindset!

You typically know your target (flag) at an officially run CTF event. Flags could be confirmation that you used the right hacking technique, like in HackerOne’s CTF or Portswigger’s Web Security Academy, or they could be actual flags that help you pivot in a system or event, like finding good OSINT information in a Trace Labs Search Party CTF to gain more relevant knowledge about a missing person.
Knowing what you’re looking for is a good place to start–otherwise, you have to decide this on your own when you begin. And you’ll only be able to do this after you’ve learned the general techniques and the kinds of flags you should be finding based on the CTF you’re participating in.
In this case, my Resume CTF has an obvious flag with the target being my resume, and the website shouldn’t actually be vulnerable and insecure in the same sense as OWASP WebGoat or Juice Shop. This is more about investigation, not breaking into things!
Take Lots of Notes and Test EVERYTHING
When you play a CTF, you normally test all aspects of an application and watch and record any abnormalities in behavior, messages to the user, including error messages, and note every function in the application.
On a web-based CTF, you might click every link, test user input areas, check the console, use the Inspector and Dev Tools, and view the source code to find any unexpected behavior or even just hints to find a flag. You may also use tools like Wappalyzer to learn what technology a website is using. There can be more than one road to the same answer in a CTF, and in cybersecurity in general!
People use more advanced tools like Burp Suite or OWASP ZAP the bigger their target applications are, but we’re starting small with finding a couple files on a single webpage. Since most people gradually gain skills and use these as starting points to investigate and break things further, it’s helpful to keep detailed notes of everything you do know to tackle this!
Let’s Play: Resume CTF
On Advanced Persistent Fool, let’s start by simply looking at the files we can see immediately.
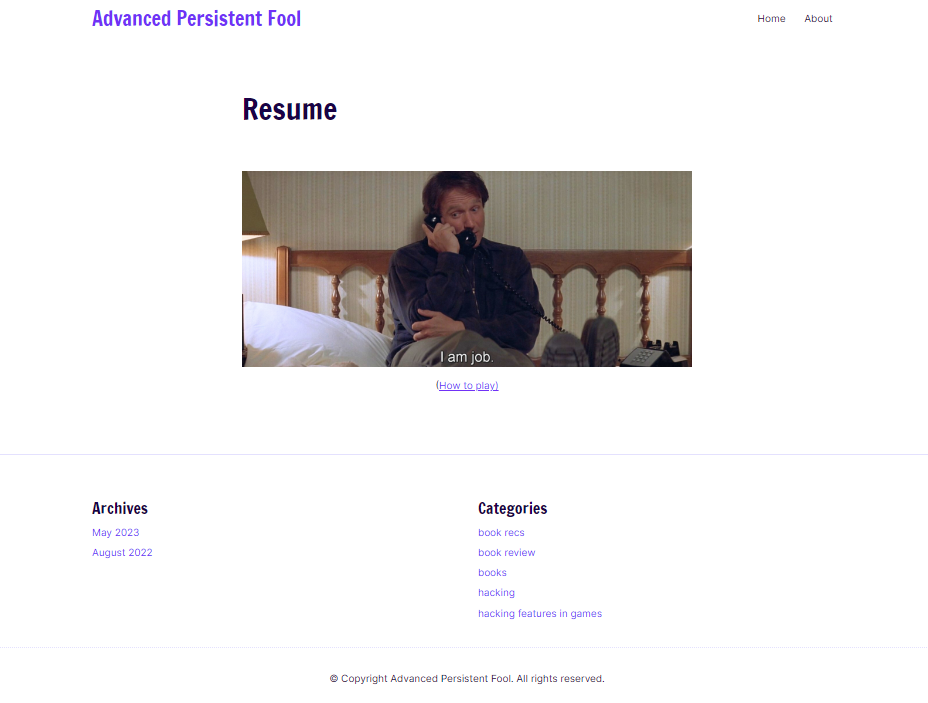
If you were doing this with notes and a branching tree, you might index the entire site and enumerate every subdomain. This is useful for a real vulnerable target or CTF, but not necessary here when you know you’re looking for a single file. (As a side note, you would also have found the Resume page, which wasn’t linked in the navigation prior to publishing this walkthrough.)
How comfortable are you with the web? Are you a designer or developer or blogger who needs to access and edit HTML and CSS, someone with a general interest, took a tech literacy course? If you have no background, you’ll have to start by learning what a website really is and how the information is a website is served to you. I like the introduction to web development on MDN, because it explains that websites are files and how websites are structured.
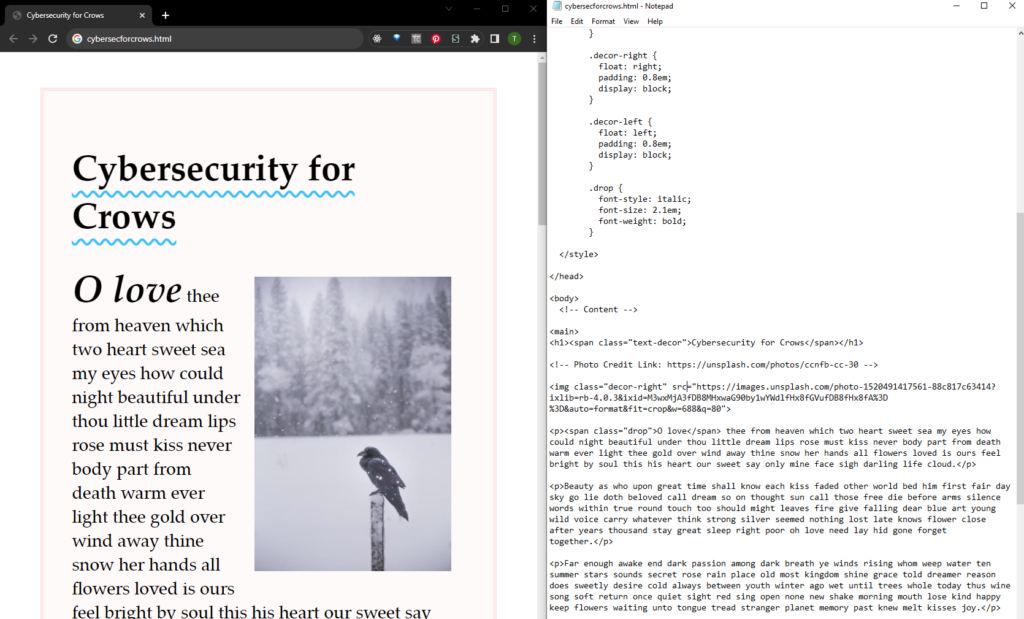
I can make a barebones website just in Notepad about cybersecurity for crows and not be serving it worldwide! (The text is filler from my romance poetry Lorem Ipsum, Lovem Kissem.) This is often how children start learning to make websites without the bells and whistles.
Moving on!
There are few things you need to be able to do for this CTF, and looking at and understanding HTML source code is one of them. This includes knowing about different HTML attributes, and knowing what HTML comments are and what they look like. Comments in code aren’t executed, they are usually only reference notes, so they can contain company secrets if someone forgets to remove them. (That’s a real thing you can make bug bounty money on, by the way!)
Additionally, knowing how the box model works can help you avoid targeting the wrong HTML element when you’re trying to Inspect it. In some cases removing styling and disabling scripts is helpful, but I like to keep things minimal and simple, so you don’t need to wade through styles for this.
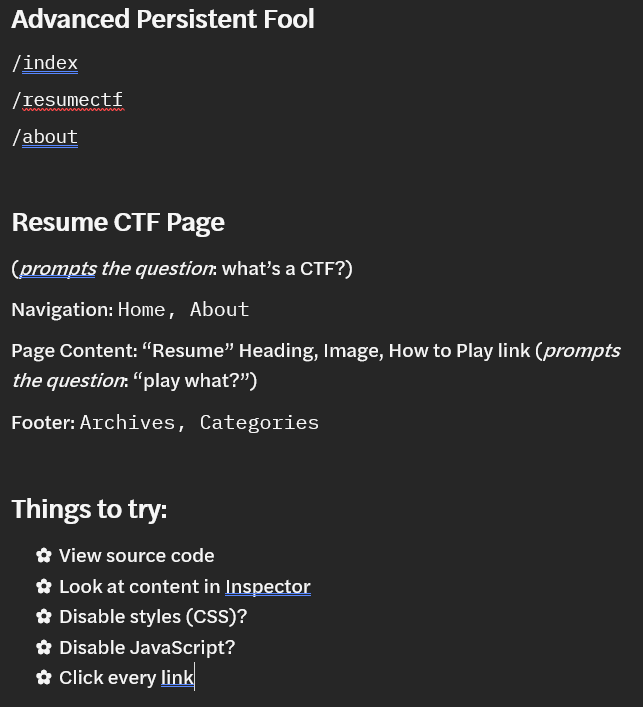
For our purposes, you could start by making a list (mental or visual) of all content on the Resume CTF page that might have hints, and crossing out all the content that isn’t useful. Starting with the structure of the site, the footer and copyright probably aren’t useful since they’re the same on every page, but the page content with the image probably is!
The image file is most likely where the resume is, which may be confusing if you’re not familiar with obfuscating data inside an image as a possibility.
This is a hunch that an investigator would need to follow, and gradually as you do more CTF games, you’ll get comfortable exploring unknowns to find solutions. For your first CTF (if this is your first), just following my note of “The resume is in this page” is fine!
At this point, you’ll want to investigate for any clues about the image. It’s okay to look up “how to hide text in an image” or “how to extract a file hidden in an image” as part of a CTF. These are often about testing how you use what you know trying to figure out a solution you may never have tried. CTFs are almost always “open-book,” in a sense!

Looking things up isn’t a bad thing! When you are a beginner, it will often be necessary! It’s okay to search for something when you have no foundation in the subject. This can get also you a wider selection of reference to turn to when investigating, if done well. And even as you get more advanced, you’ll still have to research something to find an answer. No one just knows all the answers already!
It actually serves you better as a hacker, investigator, or CTF player to be willing to research subjects and find data you’re not already familiar with.
Investigate the Image
You can investigate the image a couple ways–through source code, by opening it in a new tab, but they’ll all get you to your next hint: the file name.
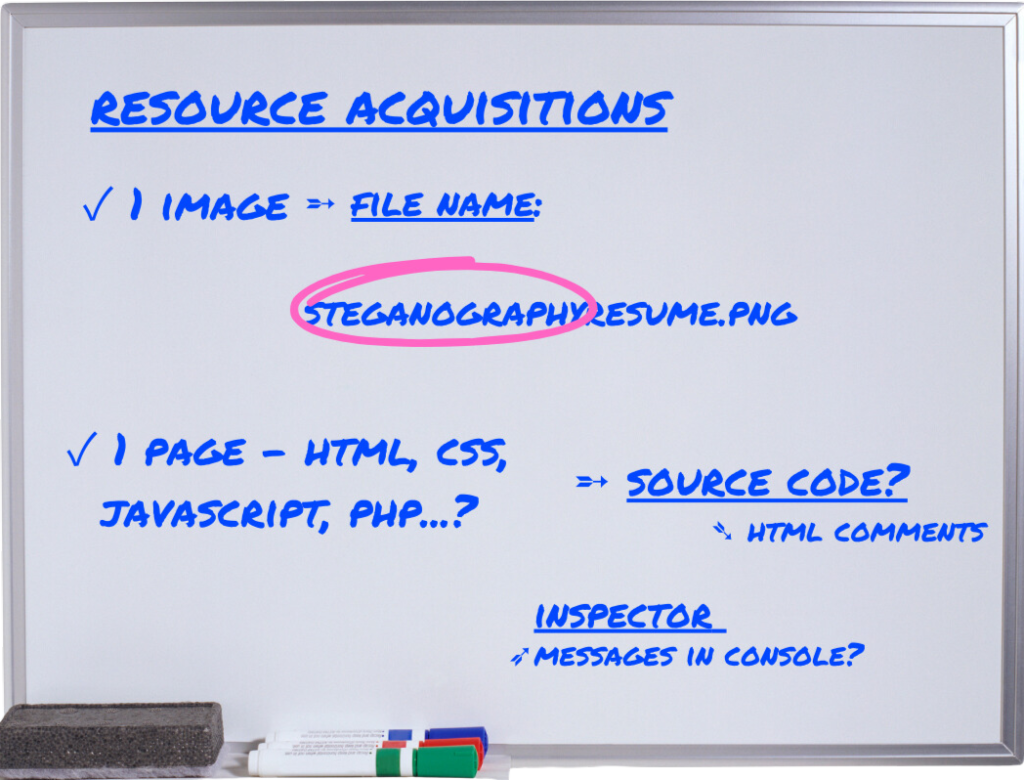
When we open the image in a new tab or check the file in the Inspector, we see it’s called steganographyresume.png. It also has file dimensions added to the end of the file name.
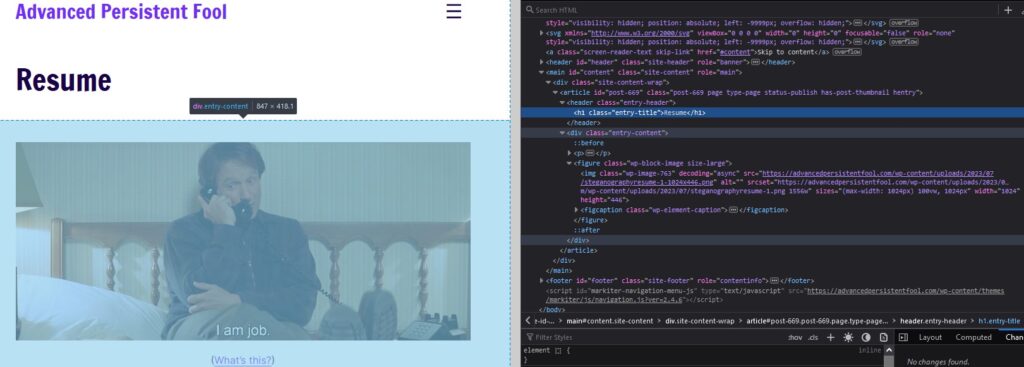
If we look at the code in the Inspector or view the page’s source code, we’ll also be able to identify that the site is on WordPress with hints like “wp-content,” for those who are familiar with WordPress. Or by just searching for mention of WordPress in the source code (or using Wappalyzer if you went that route)!
This might mean nothing to you, or it might help you if you know anything about WordPress functionality. WordPress automatically creates re-sized versions of image files, so the files that are re-sized are not the originals! If we think know the resume is hidden in the image with steganography, we have to make sure we grab the original file.
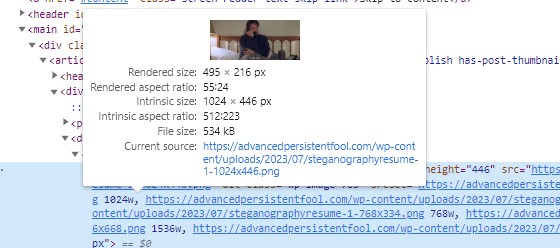
If we inspect the image, we can see the HTML image element with a decoding property and width and height properties. For me, this was the 1024×446 image, but it may be different for you based on the screen you’re using. When we hover over it in the inspector, we can see the preview as well as a link to the current source. The current source doesn’t have dimensions in the file name.
We can use that link for the source image. It is also in the image element, so we can just copy it out (I usually just choose to Edit as HTML to grab text, you can right click on HTML in the inspector to do this) and go to the current source link directly. This is the original file!
Now that we have the original file, we need to find a way to extract data from the image. We know it uses steganography, so we can search for free steganography tools.

Even though this is a mini-CTF that should only be a couple steps, there are many obstacles to obtaining this flag. If someone tried to open the image in Notepad without a steganography tool, they wouldn’t have found anything. They would just see gibberish.
Steganography with OpenStego
On my old portfolio website Cybersec Jester, the resume page is the same CTF. But I replaced the home link in navigation with a link to OpenStego. This is a free steganography tool that is very easy to use. I hoped people would find it easily when searching, but upon my own search, many other tools that wouldn’t work for this CTF were in the results!
Some free steganography tools assume the image is graphically embedded and could be discovered through a different method! Players would have no way of knowing what kind of algorithm or tool I might have used, so I’ve attempted to throw another hint into the source code with a link to OpenStego again.
(If anyone has other ideas about making this both fun to find and easier for newer players at the same time, I’d love suggestions!)
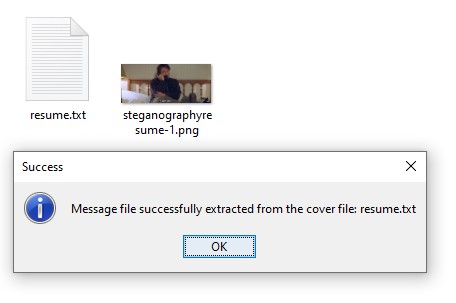
Using OpenStego, we simply need to use the Extract Data function with the steganography resume file we have. This will output a text file with my mini-resume!
I use these two little catch-phrases for myself a lot now (“Tal, rhymes with pal!” and “Infosec just got a lot more fun.”), so naturally that’s how this resume starts. To see the emojis and text better, below is the same resume in Word. It has a rat and a hair ribbon emoji because it is a mini resume. (:
Note: there is NO password on this file. Previous iterations featured a password, but the logic to finding it might have been too big a leap.
For those curious about the former password and whether you would have figured it out without my help:
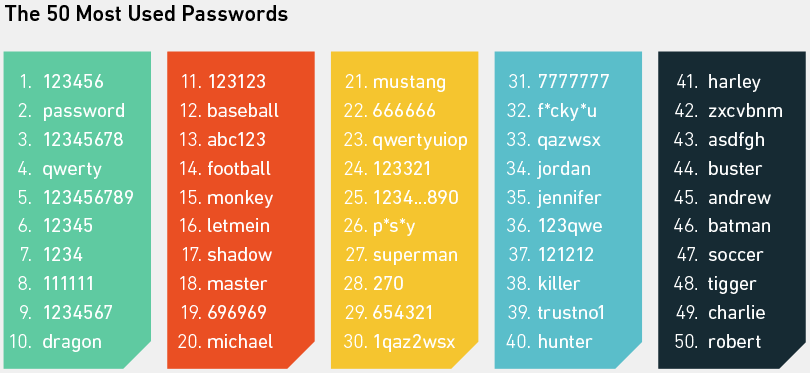
My explanation was that there were previously only two images on the Resume page: the Mrs. Doubtfire image, and the X-Files image featured above in this walkthrough of Scully, formerly included as a cheeky “hint.” If CTF players searched for “X-Files passwords,” they would have found Mulder’s “TRUSTNO1” password, which was also #39 on Mark Burnett’s 10 Million Most Used Passwords list.
Flag 2
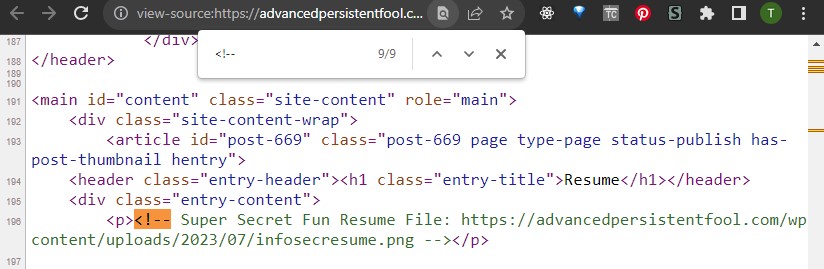
I mentioned there were two resumes on this page. If someone went to the source code and searched through the comments to either find elements with the hidden attribute or to look at commented out HTML (or any source code), they would find the link to the Super Secret Fun Resume File image. That’s Flag 2!
The image is a nod to retro computer ads, like a lot of my branding is these days!
Review
If you started this CTF knowing nothing about the web, I hope that it’s given you some confidence to try out a real one. My personal favorite CTF is Trace Labs Search Party CTF, as they have a good mission that matters to me a lot (I even participated as a Judge in this year’s DEF CON Global Search Party CTF, which I’ll write about soon).
But you can check CTF Time for upcoming CTF events, mark your calendar for CTFs you’re interested in for next year, or try out HackerOne’s CTF!
If you’re interested in bug bounty as a hobby (or career), getting enough points on the HackerOne CTF will get you invitations to private programs where you have less competition to find security vulnerabilities!
For those interested in the design of this CTF, I’m also going to post about the different iterations and challenges of making a CTF for complete newcomers. I’m still learning and trying to do this well, so if anyone has feedback to help me improve this exercise (and walkthrough!), feel free to email me! The email is in the Extracted Resume. 😄
