I love games with hacking features, but how realistic are they? Can you really crack a password at a terminal in 30 seconds? This is a companion series to my secure network design in fiction series about what hacking features in video games would look like in real life.
First, yes, there are dozens of software and hardware-based password-cracking tools out there. But the software tools are resource intensive, take much longer than 30 seconds to run, and may require an additional machine for network access. Some people’s electricity bills go up if they run John the Ripper or Hydra. (Mine did last year!) Brute forcing–or, more accurately, a dictionary attack–is, in most cases, inefficient. There are better ways of getting into systems and networks.
For the sake of making the hacking feat harder, I’ll assume you don’t have any of the cool hacking mini-tech you can easily buy online today.
Luckily for players, if you already have physical access to a machine, you don’t actually need to use cracking tools or scripts.
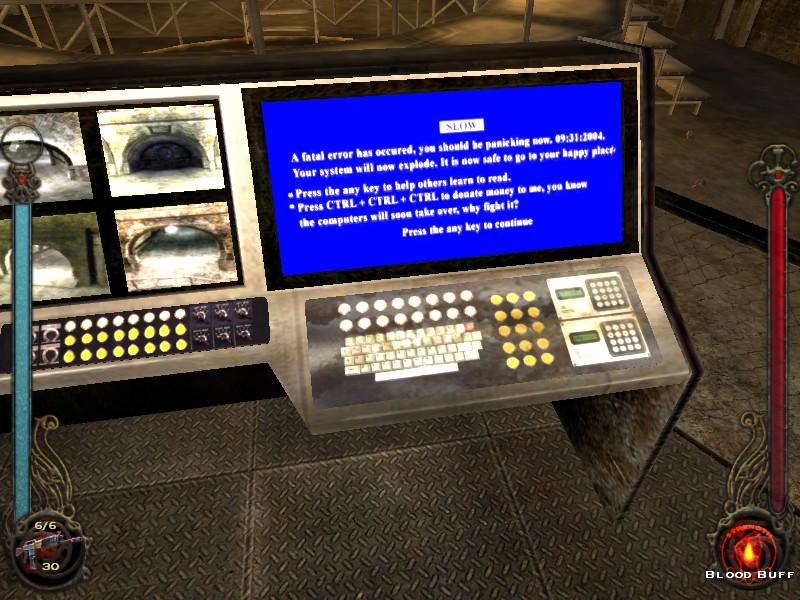
In Bloodlines, players hack into computers that are usually powered on. Players run a password-cracking script by pressing Ctrl+C and get into the machine as long as their technical skill check is high enough to succeed.
In real life, as long as you know how to get access to an administrator account, you can easily run a couple of commands to get into a machine.
how to get into a windows machine
If you have physical access to an unencrypted Windows machine, you can boot to Safe Mode without a password. You then change the password of the user via the Command Prompt.
If you don’t know the user’s name on the machine, you can find out with “net users.” It’s a quick, two-step process:
- Run “net users” in the Command prompt to know which login you want to change,
- Run “net user username hackers_new_password” to change the user’s password.
:max_bytes(150000):strip_icc():format(webp)/2017-06-163-59444d855f9b58d58a43b200.png)
If you aren’t familiar with the net command, you can learn about on Lifewire’s article featuring examples with switches (flags) and other options.
Now you can login with a changed password, rather than trying to crack the existing one. Cracking is really not an efficient method for in-the-moment hacking anyway. It’s actually more realistic to obtain information about the user or find their password lying around than attempting to brute force a password! This entire password-changing process probably takes a minute and twenty seconds total, including boot time. (I don’t know how fast computers were in 2004, but if I can find verifiable evidence on longer boot times, I’ll totally retract this statement!)
But I don’t want to stop there. That’s way too easy, right? Aren’t there more obstacles?
Sure! For one, it’s possible you can’t run Safe Mode as an Administrator on the machine.
In most cases, the computers players hack into belong to an individual, so I don’t see this occurring unless the user is a power user. Today, if the individual PCs run Windows, you can use Powershell to elevate your privileges. But Powershell wasn’t installed by default on Windows machines until Windows 7, which didn’t exist until 2009! So we might not be able to get into a computer in VtM:B if this protection is in place.
Looks like I’ve been taking Powershell for granted (not really, I’m sort of obsessed with Powershell).
creative license and bypassing encryption in 2004
The other obstacle that actually matters is encryption. Most video games don’t have encrypted disk obstacles, nor do they feature NPCs deleting or damaging their data to prevent discovery.
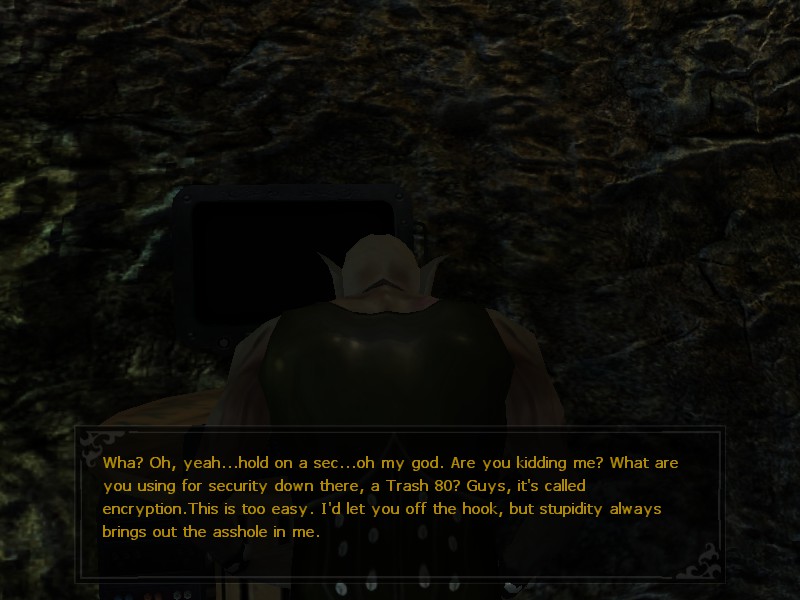
VTM:B came out in 2004. Since I wasn’t a gamer/computer-haver back then (I was a child), I’ve been researching the history of existing encryption tools that year. Outside of professionals or security enthusiasts, people didn’t really encrypt their personal computers. But devs have the luxury of creative license. Even if that was a possibility and requirement for certain machines, we still get treats like Bertram Tung’s password. It’s ‘tung.’ Like, his password is his name, y’all.
Even though the beloved, sleazy Mitnick mentions encryption when you first meet, encrypted disks aren’t a barrier for players. But who cares about that? We want to know if you can bypass encryption, if it was a real obstacle to getting into a machine!
Regular Windows machine users would have had full disk encryption capabilities from third party software in 2004. That’s when TrueCrypt released! It built on another encryption software that had been in development since the 90s. LUKS, Linux Unified Key Setup, was also created in 2004. It built upon existing encryption tools, so Linux users could also encrypt their data. (And according to my friends, Linux users typically did that by default. I have no citations for this, but I really don’t want to wade through old Linux forum discussions to find out right now.)
Can anyone get into machines that are encrypted for protection of data?
bypassing encryption
In some cases, it is possible to bypass encryption. I’ve come across videos and articles of attempts (and successes!) at bypassing Bitlocker, although some destruction of data may occur, and you might need more than one device.
hacking powered off machines
But if the computer is powered off, even if you mirrored or copied the encrypted image, you can’t get in without the necessary keys. Let’s hope that kind of information is just written on legal pads sitting around in the break room. Otherwise, the inefficient time-suck of brute forcing becomes your only option. Thank goodness most individuals–and hotels, ships carrying ancient artifacts, and bounty hunter offices–don’t encrypt their data in the game.
hacking linux machines
If you’re hacking into a Linux machine (I can’t tell what game artists base their barebones operating systems on, so I’ll cover both bases):
As long as there are no password requirements for the BIOS or GRUB, you only need another instance of Linux you can boot to–from a USB you’re presumably carrying around for this purpose–before you can get into the machine to change the root password.
If the system is protected with additional password requirements, I’m honestly not sure how else to get into a Linux machine. Most people told me it would be impossible, but as a hacker, that’s just not an acceptable answer. I flipped through several books for answers to this, and it seems like the answer is a definitive “no.” If I find out interesting entry points, I’ll update this post and make a separate post with details. I know it’s possible to change your permissions from the GRUB menu, but I don’t know if it’s possible to get into the machine this way.
no usbs, please!
As an additional possible hacking prevention, in enterprises it’s common to block USBs from running on company devices. So that USB you carried around with another Linux instance–or to hack into a device with your various USB hacking tools–can’t necessarily get you in. But this would be an unlikely precaution on a normal user’s home computer. The security-focused user would encrypt their data, so they wouldn’t have a care in the world about your physical access.
Bloodlines Hacking
What about emails? What about the systems used in the sewers?
In VtM:B, even though you have access to a computer’s main menu, email menus still need a password. So wouldn’t this be a chance to run a password-cracking script?
Possibly! Although, without any information about the user, a hacker only has common wordlists at their disposal. Brute-forcing would be a shoddy, time-exhausting option.
You also probably don’t have to worry about a user or admin being alerted to changes to an Industrial Control System or SCADA (Supervisory Control and Data Acquisition) system, such as those monitoring water and waste systems. 2FA didn’t really exist in a convenient vehicle for consumers until 2011, so even if you did a password reset request on the computer, it’s unlikely a common user would know aout the break-in.
An administrator of the computer, network, or system in the sewers would probably have been alerted, especially if it’s during odd hours (and likely via a pager system, which are still used in hospitals today for their reliability). However, players only need to get into a system once before they move on. It doesn’t really matter if the admin handles the situation via remote access afterwards.
Can’t I just look around the room?
If you prefer to snoop, that could still be fun and is definitely possible. Some people do leave their passwords sitting around near their desks, especially if the password is hard to remember.

If you know something about the user, that might help you guess passwords that aren’t hard for them to remember. If it were me, back in 2004, I probably would have implemented a phishing scam. I’d start with something as simple as asking the user for their password, stating I was from a company that manages or manufactures their software or hardware. But, depending on the target and their privacy and security knowledge, I might stoop to installing a keylogger instead (which are very easy to write). Apparently phishing scams were quite common in 2004, so the average VtM:B citizen could possibly fall victim to it.
But it’s not hard to hack into a computer you have physical access to, if they don’t protect their data. And as a powerful vampire, you don’t really have to worry about any of this. You can just threaten, manipulate, or dominate the NPC to gain entry to their systems and emails.
hacking in games series continuation
When I started writing this post, I didn’t consider this issue for any follow-up posts… Most in-game hacking features operate the exact same way. Players stand in front of a computer and run a password-cracking script or tool on the machine. So most of what I say here will also apply to other video games. In the future, I’d like to get into a more specific hack in the games and cover other technology considerations. My next post in this series will be about Deus Ex (2000)!
References & Suggested Reading
I can’t turn off the academic in me (really, that’s what this blog is for–research to get in to grad school). So I’ll always list books, studies, articles, sites, and any other media I referenced while researching my posts! But this is just a blog, so I don’t have to stick to academic formats! (:
websites & online articles
Net Command (Examples, Options, Switches, and More) by Tim Fisher on Lifewire
Disk Encryption and Encryption (Wikipedia, to verify information about encrypted disk hacking)
The History of Electronic Mail by Tom Van Vleck (researched for an email hacking section, not used)
The Evolution of Multi-Factor Authentication – The LastPass Blog
History of Phishing (KnowBe4’s Phishing resource) & Phishing (Wikipedia) – verifying phishing timelines for the suggestion
SCADA Basics from High Tide Technologies